Stan, thanks for the reply.
I have pasted below only the UNCOMMENTED sections of my gitlab.rb file.
I haven’t needed anything fancy for my GitLab instance, as I use this particular instance to store my “local lab” repositories. We have a larger corporate Git server that I use with “git bundle” to move repos from this GitLab instance.
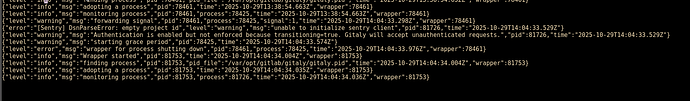
The gitaly configuration is at the bottom. I saw that the certificate path was an issue, because that certificate is not there in that directory.
However, I couldn’t find in the docs how to add this certificate in properly. The GitLab configuration is extensive, so I have only made adjustments that were outlined in the installation procedures and left the rest of the options alone.
external_url '``https://jme-gitlab.xxx.xxxxx.com``'
gitlab_rails[‘gitlab_repository_downloads_path’] = ‘tmp/repositories’
gitlab_rails[‘gitlab_shell_ssh_port’] = 22
gitlab_rails[‘gitlab_shell_git_timeout’] = 800
gitlab_rails['rack_attack_git_basic_auth'] = {
'enabled' => false,
'ip_whitelist' => ["127.0.0.1"],
'maxretry' => 10,
'findtime' => 60,
'bantime' => 3600
}
gitlab_rails['dir'] = "/var/opt/gitlab/gitlab-rails"
gitlab_rails['log_directory'] = "/var/log/gitlab/gitlab-rails"
gitlab_rails['log_group'] = nil
gitlab_rails['initial_root_password'] = "xxxxxxxxxxxxxxxxxx"
gitlab_rails['initial_shared_runners_registration_token'] = "token"
#### Toggle if root password should be printed to STDOUT during initialization
gitlab_rails['display_initial_root_password'] = true
#### Toggle if initial root password should be written to /etc/gitlab/initial_root_password
gitlab_rails['store_initial_root_password'] = true
gitlab_rails['auto_migrate'] = true
user['username'] = "git"
user['group'] = "git"
# user['uid'] = nil
# user['gid'] = nil
##! The shell for the git user
user['shell'] = "/bin/sh"
##! The home directory for the git user
user['home'] = "/home/git"
user['git_user_name'] = "GitLab"
user['git_user_email'] = "gitlab@#{node['fqdn']}"
prometheus['listen_address'] = '0.0.0.0:19090'
The gitaly configuration below…
gitlab_rails[‘internal_api_url’] = ‘https://jme-gitlab.xxx.xxxxx.com/’
gitlab_rails[‘trusted_cert_dir’] = ‘/etc/gitlab/trusted-certs’
gitaly[‘open_files_ulimit’] = 15000 # Maximum number of open files allowed for the gitaly process
##! Service name used to register Gitaly as a Consul service
gitaly[‘consul_service_name’] = ‘gitaly’
##! Semantic metadata used when registering Gitaly as a Consul service
gitaly[‘consul_service_meta’] = {}
gitaly[‘configuration’] = {
storage: [
{
name: ‘default’,
path: ‘/home/jmarcedwards/data-disk-1/git-data/repositories’
},
],
socket_path: ‘/var/opt/gitlab/gitaly/gitaly.socket’,
runtime_dir: ‘/var/opt/gitlab/gitaly/run’,
listen_addr: ‘localhost:8075’,
prometheus_listen_addr: ‘localhost:9236’,
tls_listen_addr: ‘localhost:9075’,
tls: {
certificate_path: ‘/var/opt/gitlab/gitaly/certificate.pem’,
key_path: ‘/var/opt/gitlab/gitaly/key.pem’,
},
graceful_restart_timeout: ‘1m’, # Grace time for a gitaly process to finish ongoing requests
logging: {
dir: “/var/log/gitlab/gitaly”,
level: ‘warn’,
format: ‘json’,
sentry_dsn: ‘https://<key>:<secret>@sentry.io/’,
sentry_environment: ‘production’,
},
prometheus: {
grpc_latency_buckets: [0.001, 0.005, 0.025, 0.1, 0.5, 1.0, 10.0, 30.0, 60.0, 300.0, 1500.0],
},
auth: {
token: ‘’,
transitioning: false, # When true, auth is logged to Prometheus but NOT enforced
},
git: {
catfile_cache_size: 100, # Number of ‘git cat-file’ processes kept around for re-use
bin_path: ‘/opt/gitlab/embedded/bin/git’, # A custom path for the ‘git’ executable
use_bundled_binaries: true, # Whether to use bundled Git.
signing_key: ‘/var/opt/gitlab/gitaly/signing_key.gpg’,
## Gitaly knows to set up the required default configuration for spawned Git
## commands automatically. It should thus not be required to configure anything
## here, except in very special situations where you must e.g. tweak specific
## performance-related settings or enable debugging facilities. It is not safe in
## general to set Git configuration that may change Git output in ways that are
## unexpected by Gitaly.
config: [
{ key: ‘pack.threads’, value: ‘4’ },
{ key: ‘http.http://example.com.proxy’, value: ‘http://example.proxy.com’ },
],
},
hooks: {
custom_hooks_dir: ‘/var/opt/gitlab/gitaly/custom_hooks’,
},
daily_maintenance: {
disabled: false,
start_hour: 22,
start_minute: 30,
duration: ‘30m’,
storages: [‘default’],
},
cgroups: {
mountpoint: ‘/sys/fs/cgroup’,
hierarchy_root: ‘gitaly’,
## memory_bytes: 1048576,
memory_bytes: 40000000000,
cpu_shares: 512,
cpu_quota_us: 400000,
repositories: {
count: 100,
memory_bytes: 12884901888,
## memory_bytes: 0,
cpu_shares: 128,
cpu_quota_us: 200000
},
},
concurrency: [
{
rpc: ‘/gitaly.SmartHTTPService/PostReceivePack’,
max_per_repo: 20,
},
{
rpc: ‘/gitaly.SSHService/SSHUploadPack’,
max_per_repo: 5,
},
],
rate_limiting: [
{
rpc: ‘/gitaly.SmartHTTPService/PostReceivePack’,
interval: ‘1m’,
burst: 10,
},
{
rpc: ‘/gitaly.SSHService/SSHUploadPack’,
interval: ‘1m’,
burst: 5,
},
],
pack_objects_cache: {
enabled: true,
dir: ‘/var/opt/gitlab/git-data/repositories/+gitaly/PackObjectsCache’,
max_age: ‘5m’,
},
}
letsencrypt['auto_renew'] = true
letsencrypt['auto_renew_hour'] = 0
letsencrypt['auto_renew_minute'] = nil # Should be a number or cron expression, if specified.
letsencrypt['auto_renew_day_of_month'] = "*/4"
letsencrypt['auto_renew_log_directory'] = '/var/log/gitlab/lets-encrypt'