Currently trying to get dependency_scanning with Trivy and Gitlab working (free self hosted version v17.0.1). While the scanning works fine like that in the pipeline:
vulnerability-scan:
image: aquasec/trivy:latest
stage: vulnerability-scan
script:
- trivy fs --scanners vuln --severity HIGH,CRITICAL --format template --template "@/contrib/gitlab.tpl" Gemfile.lock --output gitlab_trivy_gemfile_report.json
artifacts:
when: always
reports:
dependency_scanning: gitlab_trivy_gemfile_report.json
rules:
- if: '$CI_PIPELINE_SOURCE == "merge_request_event"'
when: always
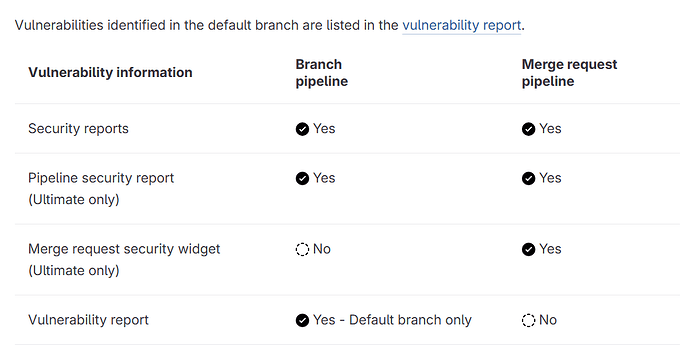
and while the gitlab_trivy_gemfile_report.json file can be downloaded within the Gitlab merge request once the scan is over, I do not see any graphical results in Gitlab Merge request itself like the vulnerablity report. Is my command wrong? Do I need to add something more? I thought using the correct template, as I do, would actually do the trick, but something is still missing.
best
Martin