I set up the gitlab-runner kubernetes executor to run with a non root user “gitlab-runner”
Problem to solve
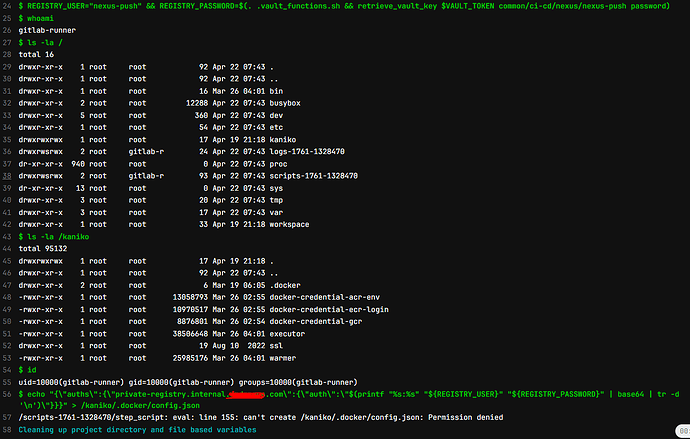
i get it working for all images except for Kaniko image , i build a custom kaniko image from the official kaniko image and i put the new user owner of the folder “/kaniko” .
But when i run my pipeline i see that all the folder and subfolder of “/” is owner by root inclusing my “/kaniko”
Wht i get override the folders of my image ? any idea
Configuration
image:
registry: registry.gitlab.com
image: gitlab-org/gitlab-runner
rbac:
create: true
rules:
- apiGroups: ["*"]
resources: ["*"]
verbs: ["*"]
clusterWideAccess: true
serviceAccountName: gitlab-runner
podSecurityPolicy:
enabled: false
resourceNames:
- gitlab-runner
runners:
config: |
[[runners]]
builds_dir = "/tmp/builds"
environment = ["HOME=/tmp"]
[runners.kubernetes]
namespace = "{{ item.namespace }}"
image = "private-registry.internal.custom.com/custom-gitlab-runner-jdk11:latest"
tls_verify = false
poll_timeout = 3600
output_limit = 50000000
allowed_pull_policies = ["always", "if-not-present"]
[runners.kubernetes.pod_security_context]
run_as_non_root = true
run_as_user = 10000
run_as_group = 10000
fs_group = 10000
[runners.kubernetes.init_permissions_container_security_context]
run_as_user = 10000
run_as_group = 10000
[runners.kubernetes.node_selector]
"type"="runner"
[runners.kubernetes.node_tolerations]
"type=runner" = "NoSchedule"
[runners.cache]
Type = "s3"
Path = "runner"
Shared = true
[runners.cache.s3]
ServerAddress = "oos.eu-west-2.outscale.com"
BucketName = "{{ item.bucket_name | default("k8s-gitlab-runner-cache") }}"
BucketLocation = "eu-west-2"
Insecure = false
AuthenticationType = "access-key"
name: "{{ item.name }}"
privileged: true
secret: "{{ item.secret_name }}"
cache:
secretName: s3access
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: false
runAsNonRoot: true
privileged: false
capabilities:
drop: ["ALL"]
podSecurityContext:
runAsUser: 100
fsGroup: 65533
supplementalGroups: [10000]
volumes: []
Gitlab-ci
build-job:
stage: build-image-with-kaniko
image:
name: private-registry.internal.custom.com/gitlab-runner-kaniko:1.1.60-SNAPSHOT
pull_policy: always
entrypoint: [""]
script:
- echo "{\"auths\":{\"private-registry.custom.internal.com\":{\"auth\":\"$(printf "%s:%s" "${REGISTRY_USER}" "${REGISTRY_PASSWORD}" | base64 | tr -d '\n')\"}}}" > /kaniko/.docker/config.json
- /kaniko/executor
--context .
--dockerfile Dockerfile
--destination private-registry.internal.custom.com/dpd-ubuntu:latest
variables:
tags:
- gitlab-runner-rootless
Versions
-
- Self-managed with Kubernetes executor : gitlab-runner 16.3.3
Thank you for your help