Here is the .gitlab-ci.yml file
include:
- template: Security/SAST.gitlab-ci.yml
- template: Security/Dependency-Scanning.gitlab-ci.yml
- template: Security/Secret-Detection.gitlab-ci.yml
- template: Security/License-Scanning.gitlab-ci.yml
default:
tags:
- internal
variables:
THRESHOLD_CODE_COVERAGE: 80
VAR_version_code: ${versioncode}
SAST_EXCLUDED_ANALYZERS: “spotbugs”
DS_EXCLUDED_ANALYZERS: “gemnasium-maven”
SAST_REPORT_FILE: “gl-sast-report.json”
GEMNASIUM_DS_REPORT_FILE: “gl-dependency-scanning-report.json”
COVERAGE_REPORT_FILE: “Pocket/coverage/cobertura-coverage.xml”
COVERAGE_REPORT_JSON: “Pocket/coverage/coverage-summary.json”
LICENSE_SC_REPORT_FILE: “gl-license-scanning-report.json”
SECRET_DETECTION_REPORT_FILE: “gl-secret-detection-report.json”
SAST_EXCLUDED_PATHS: Pocket/src/components/LoadingIndicator/reducer.js,Pocket/src/common/store/typeSafe.js,package-lock.json
SECRET_DETECTION_EXCLUDED_PATHS: .gitlab-ci.yml
DS_EXCLUDED_PATHS: Pocket/yarn.lock,Pocket/src/components/LoadingIndicator/reducer.js,Pocket/src/common/store/typeSafe.js,package-lock.json
image: reactnativecommunity/react-native-android:5.4
#stages
stages:
- test
- build
- bundle_build
- release
#ESLINT-SAST ANALYZER
eslint-sast:
stage: test
allow_failure: false
artifacts:
paths:
- $SAST_REPORT_FILE
expire_in: 1 day
#GEMNASIUM-DEPENDENCY_SCANNING ANALYZER
gemnasium-dependency_scanning:
stage: test
allow_failure: false
artifacts:
paths:
- $GEMNASIUM_DS_REPORT_FILE
expire_in: 1 day
#VERIFYING GEMNASIUM-DEPENDENCY_SCANNING VULNERABILITIES
verify-gemnasium-vulnerabilites:
stage: test
rules:
- if: $CI_COMMIT_TAG
when: never
needs:
- job: “gemnasium-dependency_scanning”
variables:
GIT_STRATEGY: none
cache: {}
before_script:
- sudo apt-get update
- sudo apt-get -y install jq
script:
- |
if [ -f “$GEMNASIUM_DS_REPORT_FILE” ]; then
if [[ “$CI_COMMIT_REF_NAME” = “main” ]]; then
if [[ “$(jq “.vulnerabilities | length” $GEMNASIUM_DS_REPORT_FILE)” -gt 0 ]]; then
echo “Vulnerabilities detected. Please check”
exit 1
fi
else
if [[ “$(jq “.vulnerabilities.severity” $GEMNASIUM_DS_REPORT_FILE | grep “High|Critical” | wc -l)” -gt 0 ]]; then
echo “High/Critical Vulnerabilities present”
exit 1
fi
fi
fi
#LICENSE_SCANNING ANALYZER
license_scanning:
stage: test
allow_failure: false
artifacts:
paths:
- $LICENSE_SC_REPORT_FILE
expire_in: 1 day
#VERIFYING LICENSE_SCANNING VULNERABILITIES
verify-license-scan-vulnerabilites:
stage: test
rules:
- if: $CI_COMMIT_TAG
when: never
needs:
- job: “license_scanning”
variables:
GIT_STRATEGY: none
cache: {}
before_script:
- sudo apt-get update
- sudo apt-get -y install jq
script:
- |
if [ -f “$LICENSE_SC_REPORT_FILE” ]; then
if [[ “$CI_COMMIT_REF_NAME” = “main” ]]; then
if [[ “$(jq “.vulnerabilities | length” $LICENSE_SC_REPORT_FILE)” -gt 0 ]]; then
echo “Vulnerabilities detected. Please check”
exit 1
fi
else
if [[ “$(jq “.vulnerabilities.severity” $LICENSE_SC_REPORT_FILE | grep “High|Critical” | wc -l)” -gt 0 ]]; then
echo “High/Critical Vulnerabilities present”
exit 1
fi
fi
fi
#NODEJS-SCAN-SAST ANALYZER
nodejs-scan-sast:
stage: test
allow_failure: false
artifacts:
paths:
- $SAST_REPORT_FILE
expire_in: 1 day
#SECRET_DETECTION ANALYZER
secret_detection:
stage: test
allow_failure: false
artifacts:
paths:
- $SECRET_DETECTION_REPORT_FILE
expire_in: 1 day
#VERIFYING SECRET_DETECTION VULNERABILITIES
verify-secret-detection-vulnerabilites:
stage: test
rules:
- if: $CI_COMMIT_TAG
when: never
needs:
- job: “secret_detection”
variables:
GIT_STRATEGY: none
cache: {}
before_script:
- sudo apt-get update
- sudo apt-get -y install jq
script:
- |
if [ -f “$SECRET_DETECTION_REPORT_FILE” ]; then
if [[ “$CI_COMMIT_REF_NAME” = “main” ]]; then
if [[ “$(jq “.vulnerabilities | length” $SECRET_DETECTION_REPORT_FILE)” -gt 0 ]]; then
echo “Vulnerabilities detected. Please check”
exit 1
fi
else
if [[ “$(jq “.vulnerabilities.severity” $SECRET_DETECTION_REPORT_FILE | grep “High|Critical” | wc -l)” -gt 0 ]]; then
echo “High/Critical Vulnerabilities present”
exit 1
fi
fi
fi
#SEMGREP-SAST ANALYZER
semgrep-sast:
stage: test
allow_failure: false
artifacts:
paths:
- $SAST_REPORT_FILE
expire_in: 1 day
#VERIFYING SAST VULNERABILITIES
verify-sast-vulnerabilites:
stage: test
rules:
- if: $CI_COMMIT_TAG
when: never
#Added artifacts
artifacts:
name: sast
paths:
- gl-sast-report.json
reports:
sast: gl-sast-report.json
when: always
needs:
# - job: “eslint-sast”
- job: “nodejs-scan-sast”
- job: “semgrep-sast”
variables:
GIT_STRATEGY: none
cache: {}
before_script:
- sudo apt-get update
- sudo apt-get -y install jq
script:
- echo $(pwd)
- ls
- |
if [ -f “$SAST_REPORT_FILE” ]; then
if [[ “$CI_COMMIT_REF_NAME” = “main” ]]; then
if [[ “$(jq “.vulnerabilities | length” $SAST_REPORT_FILE)” -gt 0 ]]; then
echo “Vulnerabilities detected. Please check”
exit 1
fi
else
if [[ “$(jq “.vulnerabilities.severity” $SAST_REPORT_FILE | grep “High|Critical” | wc -l)” -gt 0 ]]; then
echo “High/Critical Vulnerabilities present”
exit 1
fi
fi
fi
#TEST AND CODE-COVERAGE
test:
stage: test
coverage: /All files[^|]|[^|]\s+([\d.]+)/
script:
- cd Pocket && yarn install
- yarn test:ci
artifacts:
expire_in: 1 week
paths:
- $COVERAGE_REPORT_JSON
reports:
junit:
- Pocket/junit.xml
coverage_report:
coverage_format: cobertura
path: $COVERAGE_REPORT_FILE
#verifying code-coverage
verify-code-coverage:
stage: test
rules:
- if: $CI_COMMIT_TAG
needs:
- job: “test”
variables:
GIT_STRATEGY: none
cache: {}
before_script:
- sudo apt-get update
- sudo apt-get -y install jq
script:
- echo $(pwd)
- ls
# - ls */
- |
if [[ -f “$COVERAGE_REPORT_JSON” ]]; then
CODE_COVERAGE_VALUE=$(jq “.total.statements.pct” $COVERAGE_REPORT_JSON | cut -d’.’ -f1)
echo “code coverage is $CODE_COVERAGE_VALUE”
if [[ $CODE_COVERAGE_VALUE -lt $THRESHOLD_CODE_COVERAGE ]];
then
echo “The code coverage is below $THRESHOLD_CODE_COVERAGE%”
exit 1
else
echo “The code coverage is great and above $THRESHOLD_CODE_COVERAGE%”
fi
fi
#BUILD
build:
stage: build
before_script:
- echo “JOB_ID=$CI_JOB_ID” >> build.env
- echo $JOB_ID
script:
- cd Pocket && yarn install
- cd android && chmod +x gradlew
- ./gradlew clean
- ./gradlew assembleRelease
artifacts:
paths:
- Pocket/android/app/build/outputs/
expire_in: never
reports:
dotenv: build.env
only:
- develop
- release
#- hotfix
- main
bundle_build:
stage: build
needs:
- job: build
artifacts: true
script:
- cd Pocket && yarn install
- cd android && chmod +x gradlew
- ./gradlew bundleRelease
- cd app/build/outputs/bundle/release
artifacts:
paths:
- Pocket/android/app/build/outputs/bundle/release
expire_in: never
only:
- main
create_version:
stage: build
needs:
- job: “build”
script:
- |
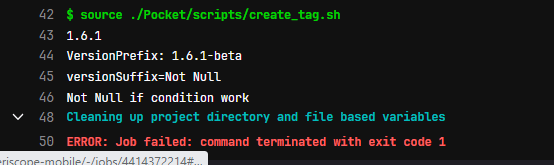
source ./Pocket/scripts/create_tag.sh
only:
- develop
- release
- hotfix
- main
#Release job
release_job:
stage: release
image: registry.gitlab.com/gitlab-org/release-cli:latest
rules:
- if: $CI_COMMIT_TAG
when: always
needs:
- job: build
artifacts: true
script:
- echo $JOB_ID
release:
name: “$CI_COMMIT_TAG”
tag_name: “$CI_COMMIT_TAG”
description: “release”
ref: “$CI_COMMIT_SHA”
assets:
links:
- name: “Periscope-mobile-outputs-apk”
url: “https://gitlab.com/invafresh/platform/uxui/periscope-mobile/-/jobs/${JOB_ID}/artifacts/browse/Pocket/android/app/build/outputs/apk/release/”
- name: “Periscope-mobile-outputs-aab”
url: “https://gitlab.com/invafresh/platform/uxui/periscope-mobile/-/jobs/${JOB_ID}/artifacts/browse/Pocket/android/app/build/outputs/bundle/release/”