GitLab is an awesome tool for DevOps and really simplifies your cloud operation life!
I am also new to GitLab and appreciate all the articles you guys provided to help me understand how to use GitLab correctly. So, I would like to share my configuration of how I can access my EKS cluster created by GitLab AudoDevOPs.
I know some of you may have concerns to use “kubectl” to access the EKS cluster created by GitLab, and it might cause you some security-issues which are not covered in this article. For my case, I would like to have “kubectl” to understand my deployments with more details.
If you want to do the same thing as I do, let’s start!
Make your EKS cluster Ready!
- use GitLab to create your EKS cluster - tutorial is here
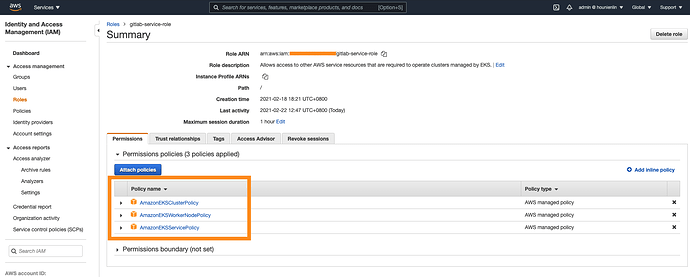
- when you create the service role for GitLab, you should manually add 2 more policies. Otherwise, you might have the same failure as I had on adding worker nodes.
- AmazonEKSClusterPolicy,
- AmazonEKSServicePolicy
- AmazonEKSWorkerNodePolicy (optional) - I would like to know my work nodes status as well.
If you have any issues, please go ahead to check the AWS cloud formation stack event for more details. The issues I had during my creation are fixed and listed for your reference. The cloud Formation stack events are very useful for checking our cloud creation states and issues.
- unable to add work node
- unable to create EKS cluster/work nodes due to no sufficient instances.
- check your K8S cluster after you create it via the GitLab console as below. In my figure, I also installed Prometheus add-on for monitoring the nodes health.
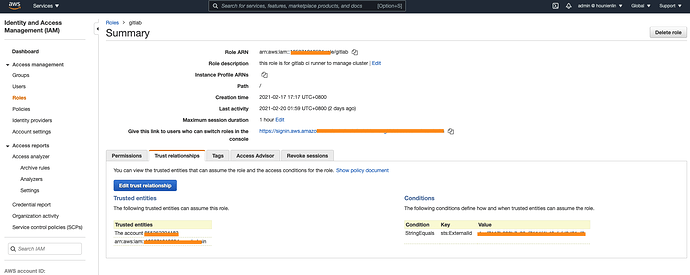
- Add your IAM user into the “trusted relationship” of the provision role that Gitlab uses as below:
- Edit the trusted relationship
- Attache below settings.
You have to use your own [AWS account ID] and [IAM user name]
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::[AWS account ID]:user/[IAM user name]"
},
"Action": "sts:AssumeRole"
}
]
- update your kubeconfig via aws cli
You have to use your own [eks-cluster-name], [eks-cluster-region], [your-aws-account-id], [your-gitlab-provision-role-name]
$ aws eks update-kubeconfig --name [eks-cluster-name] --region [eks-cluster-region] --role-arn arn:aws:iam::[your-aws-account-id]:role/[your-gitlab-provision-role-name]
outputs:
Updated context arn:aws:eks:us-east-1:33333333333334:cluster/gaia-rd-goteam-dev-3 in /Users/hounienlin/.kube/config
- check your EKS cluster via kubectl
$ alias k=kubectl
$ k cluster-info
$ k get svc,no

Now you can use kubectl to access your EKS cluster created by GitLab.
If you have other issues or feedback, please feel free to let me know. I will do my best to help.